
Emerging Trends in System Administration: The SysAdmin Revolution
In the field of system administration, several emerging trends and innovations are shaping the future. These include the widespread use of cloud-native technologies to deliver services and applications, the adoption of DevSecOps practices for more efficient and collaborative system development and operations, the use of artificial intelligence (AI) and machine learning (ML) for automation and predictive maintenance, the rise of edge computing for faster data processing, and the increasing focus on Internet of Things (IoTs). Keeping abreast of these trends enhances system administration practices allowing the profession to stay competitive and lucrative in the ever-evolving technology landscape.

Cloud-Native Technologies
Cloud computing has revolutionised the methods of managing operations and keeping data in business organisations. The technology allows the organisation to access resources and applications remotely through the internet, thus eliminating the need for physical infrastructure, and enabling organisations to streamline their operations effectively. Cloud-native technologies are those built specifically for the cloud, using various cloud principles microservices, containers, orchestration, serverless, and observability. Such technologies enable system administrators to deploy, manage, and monitor applications in a more agile, flexible, and cost-effective way and leverage the cloud’s native features and tools to automate, optimise, and secure system administration tasks.
Consequently, system administrators need to be adept in the management of cloud platforms and be familiar with managing and optimising Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) offerings for them to perform their jobs effectively. The transition to cloud environments requires a deep understanding of resource allocation, cost management, and data migration strategies among system administration staff which can be obtained through upskilling and continuous educational programs.
Infrastructure as Code (IaC)
Infrastructure as Code (IaC) refers to a methodology that is employed in the deployment of cloud infrastructure such as virtual machines and load balances. Redhat (2022) defines IaC as the management and provisioning of infrastructure as code rather than through manual processes. IaC is extensively gaining popularity in the system administration space. It refers to a method of managing and provisioning IT infrastructure using machine-readable code and configuration files as opposed to manual processes and Graphical User Interface (GUI) tools.
The IaC method allows system administrators to automate, standardise, and document day-to-day system administration tasks, such as creating, updating, and deleting servers, networks, and storage. In addition, by coding the configuration details into delivery, IaC assists in preventing unauthorised changes in system configuration thus simplifying system security processes in the organisation. System administrators can also apply to the enforcement of security policies, standards and best practices in their environments. The key outcomes in the application of IaC include marked increases in productivity, scalability, efficiency, and consistency, and the reduction in human errors.
DevSecOps
Another emerging trend in the field of system administration is DevSecOps. DevSecOps is an extension of DevOps that incorporates security into every stage of the software development lifecycle. This approach ensures the security of the application from the start to the end of the development cycle.
The DevSecOps approach seeks to ensure the integration of software development, operations and security to deliver secure software features faster than the traditional methods while maintaining quality. This is achieved through the deployment of software into production systems through small, continuous iterations making it easier for system administrators to closely monitor the integrated systems. Through the adoption of DevSecOps, system administrators can improve system administration workflow, quality, and performance and align their security objectives with those of the entire organisation.
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML have also found their way into the system administration discipline by allowing machines to undertake critical tasks that are ordinarily done by humans. These tasks include reasoning, learning, and decision the application of AI/ML one of the key emerging trends in enhancing system administration capabilities. They can be applied in a variety of ways including automation, predicting and preventing failures, anomalies, and threats; optimising data analysis and performance and enhancing user experience and satisfaction.
Intuitive navigation brought about by AI/ML is critical to enable users to find information complete tasks quickly and make the appropriate decisions timely. Additionally, system administrators can deploy AI and ML tools and platforms or develop their solutions to develop algorithms required to improve system administration outcomes and significantly enhance system reliability, security, and efficiency. For example, SentinelOne applies predictive analytics to find irregularities in client systems or known security breaches and notify system administrators for follow-ups.
Edge Computing
Edge computing is an emerging trend in system administration that involves the processing and analysis of data closer to the source in the form of users or devices. This approach is favoured as it helps in reducing latency and enabling real-time decision-making and is particularly relevant in scenarios with limited connectivity or sensitive data requirements. For system administrators, edge computing provides valuable opportunities in effectively administering distributed environments and remote work and collaboration processes in business organisations.
By bringing computation and data storage closer sources instead of placing reliance on centralised servers or clouds, edge computing can assist in improving system administration performance, reliability, and security. This is especially true for use cases that require low latency, high bandwidth, or real-time processing such as IoT and smart devices, Augmented Reality/Virtual Reality (AR/VR), autonomous vehicles and drones, gaming and streaming.
Internet of Things (IoT)
The IoT refers to the interconnection of devices over the internet enabling them to share data. The technology opens up exciting opportunities for organisations to enhance their system administration capabilities further. Statista estimates the number of IoT-connected devices to reach 75.44 billion by the year 2025. This demonstrates the exponential growth of IoT technology and its impact on system administration duties and responsibilities. This growth means that as more devices get connected to the internet, system administrators are faced with new and unique opportunities and challenges in their work. IoT adds complexities to system infrastructures due to the huge volume and diversity of the devices involved and their integrations.
Despite the above complexity, system administrators have to ensure that seamless, secure communication between these devices., IoT-enabled devices can be used to collect data on various aspects of business operations, such as facility usage, energy consumption, and employee behaviour patterns which can be used in perfecting system administration processes. It is therefore crucial for contemporary system administrators must understand not only the technology behind IoT and its associated protocols but also the challenges and opportunities that this technology brings in system administration duties.
Automation and Scripting
Automation and scripting have become integral components of modern system administration and the capability to automate repetitive tasks through scripts improves system efficiency while at the same time the likelihood of human error. The system administration field has also witnessed an increase in automation and scripting in recent years.
System administration scripts are programs or commands that can execute a series of instructions on a system. These scripts are written in a variety of programming languages such as PowerShell, Bash and Python. System administrators must be proficient in scripting languages and have the necessary skills and capabilities to assess the development, debugging, and deployment of scripts to manage a wide array of system administration tasks. The diagram below depicts the process involved in the automation of system administration for an SQL database.
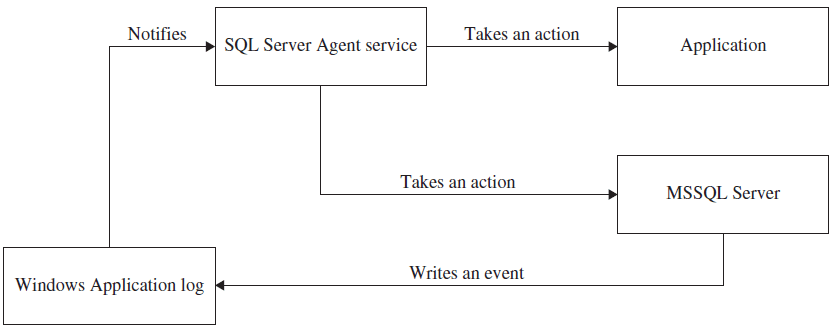
Image Source: https://www.w3computing.com/sqlserver2012/automating-system-administration-tasks-starting-sql-server-agent/
As depicted in the diagram above, the system administrator automates database tasks that can occur following a regular schedule. For instance, a database backup exercise can be scheduled to occur at 1300hrs daily. The MSSQL Server service writes events to the Windows application log, which in turn stores all application and system messages of Windows operating systems and messages of their components and notifies the SQL Server Agent about existing events. The SQL Server Agent takes the necessary action in response to all the notifications received through the Windows Application log.
Tasks that can be automated are wide-ranging encompassing the automation of backups up to system monitoring. An example of such an automation tool is Attune. Compatible with both MacOS and Windows operating systems, AttuneOps empowers system administrators to automate repetitive tasks seamlessly and faster at the same time providing system administrators with greater control and flexibility over their duties and responsibilities.
Conclusion
As can be deduced from the above discussion, the future of system administration is multi-faceted, shaped by emerging trends and as such today’s system administrators are expected to be at the forefront of technological innovations ranging from proactively implementing advanced security protocols in their daily activities to managing data using advanced technological solutions.
Grasping the workings of such technologies has increasingly become non-negotiable for the system administration profession as businesses look to bolster their operational efficiencies and cybersecurity posture.
References
- https://cibrwarriors.com/the-future-of-system-administration-and-its-impact-on-it-staffing/
- https://moldstud.com/articles/p-the-future-of-system-administration-in-university-environments-emerging-trends-and-opportunities
- https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2023/top-risks-and-rewards-of-moving-to-the-cloud

Comments